Senserva Premier Partners
Bulletproof, with locations across North America and around the globe, is a trusted leader in IT security and compliance solutions. With decades of expertise in various industries, including gaming organizations, tribal organizations, government agencies, and state organizations, Bulletproof mitigates risk and improves client processes, systems, and business infrastructure. Bulletproof is also a member of the Microsoft Intelligent Security Association (MISA)
The goal of Bulletproof and Senserva's partnership is to provide world-class security solutions to Microsoft customers to protect them from modern cyberthreats by identifying opportunities to develop new solutions that further enhance Microsoft Security products.
Wade Dauphinee, Senior Vice President of Bulletproof's Managed Security Services division, said, "I firmly believe that strategic collaborations are the key to delivering unparalleled value to our customers. Our partnership with Senserva has been instrumental in co-creating cutting-edge security solutions, harnessing the power of Microsoft technologies. This dynamic synergy not only enhances our capabilities but also guarantees our customers receive tailored, forward-thinking security solutions that seamlessly adapt to their ever-evolving needs."
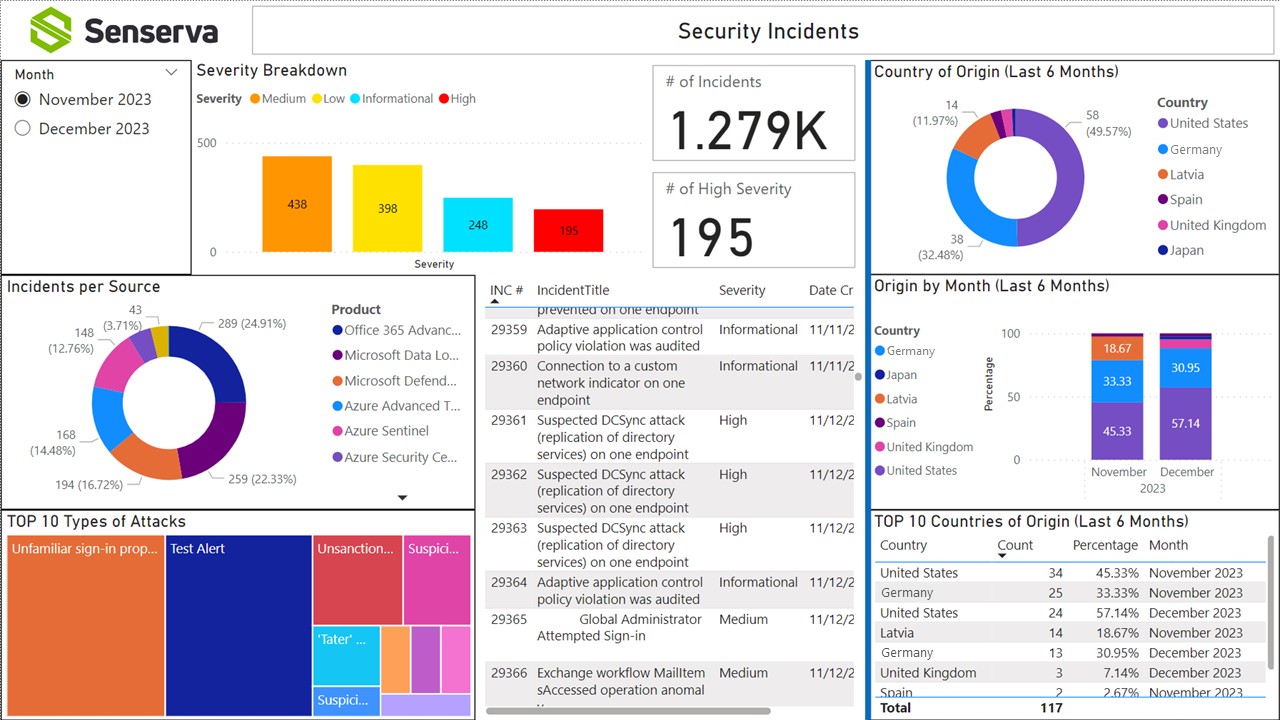
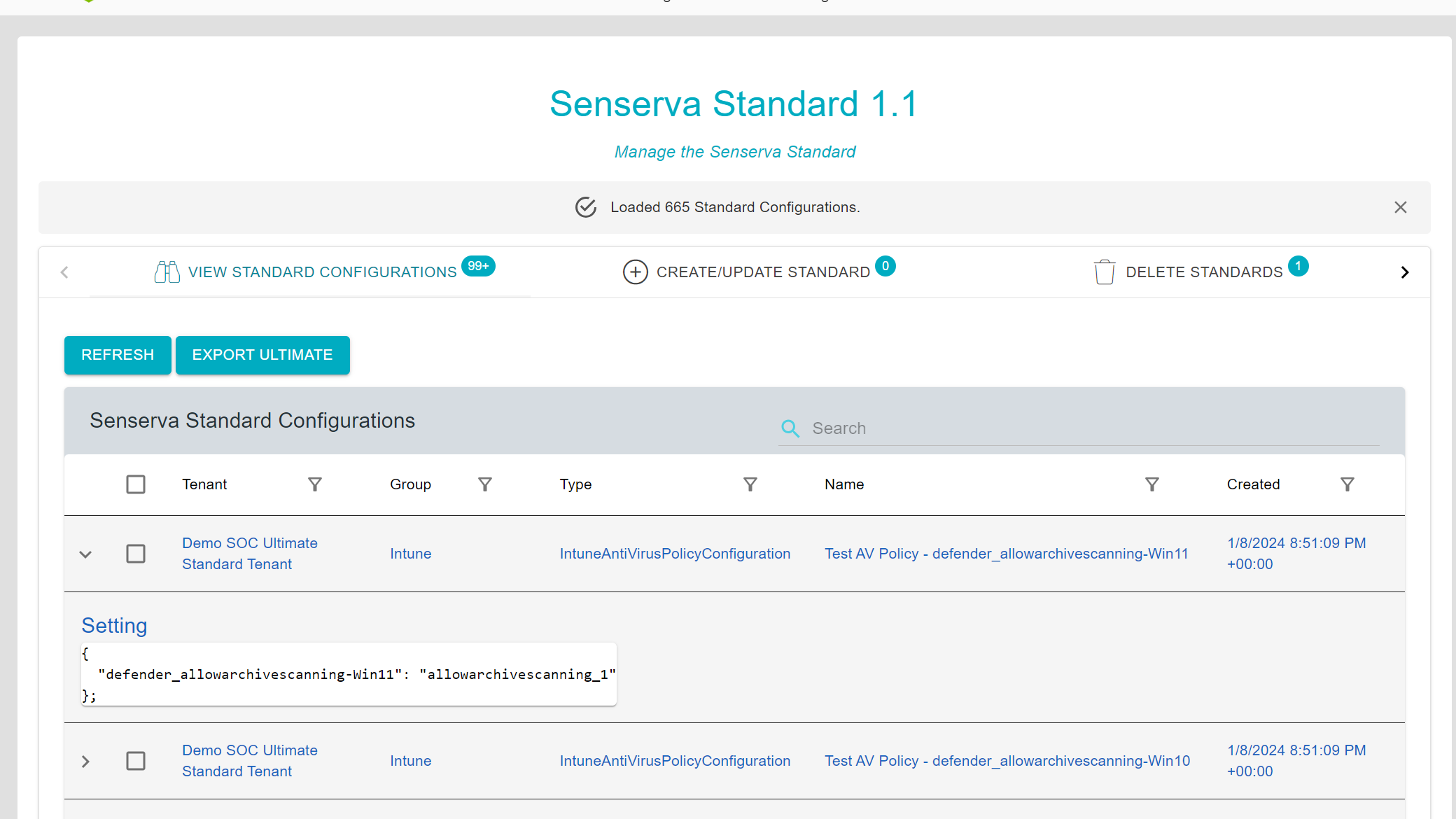
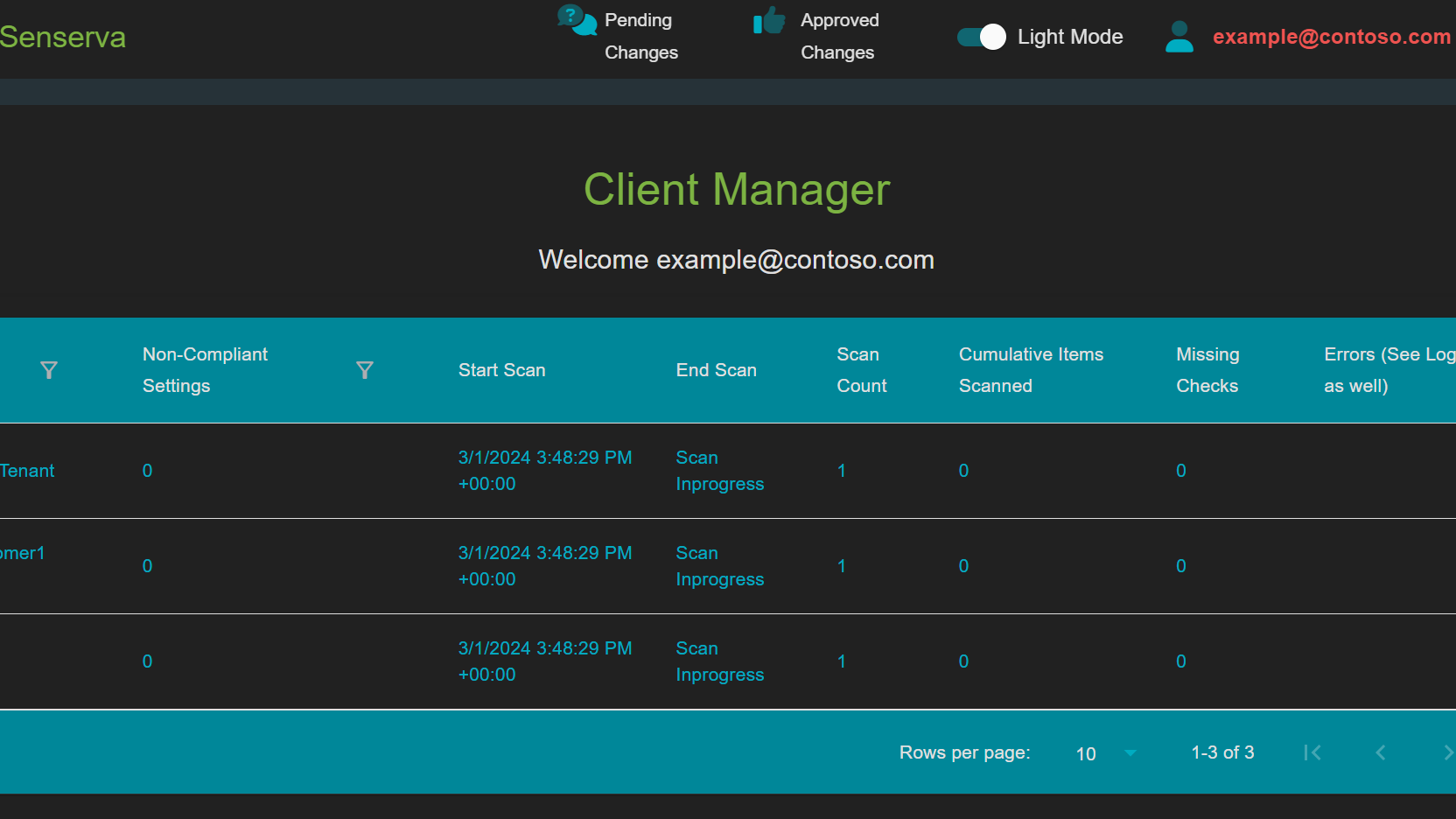
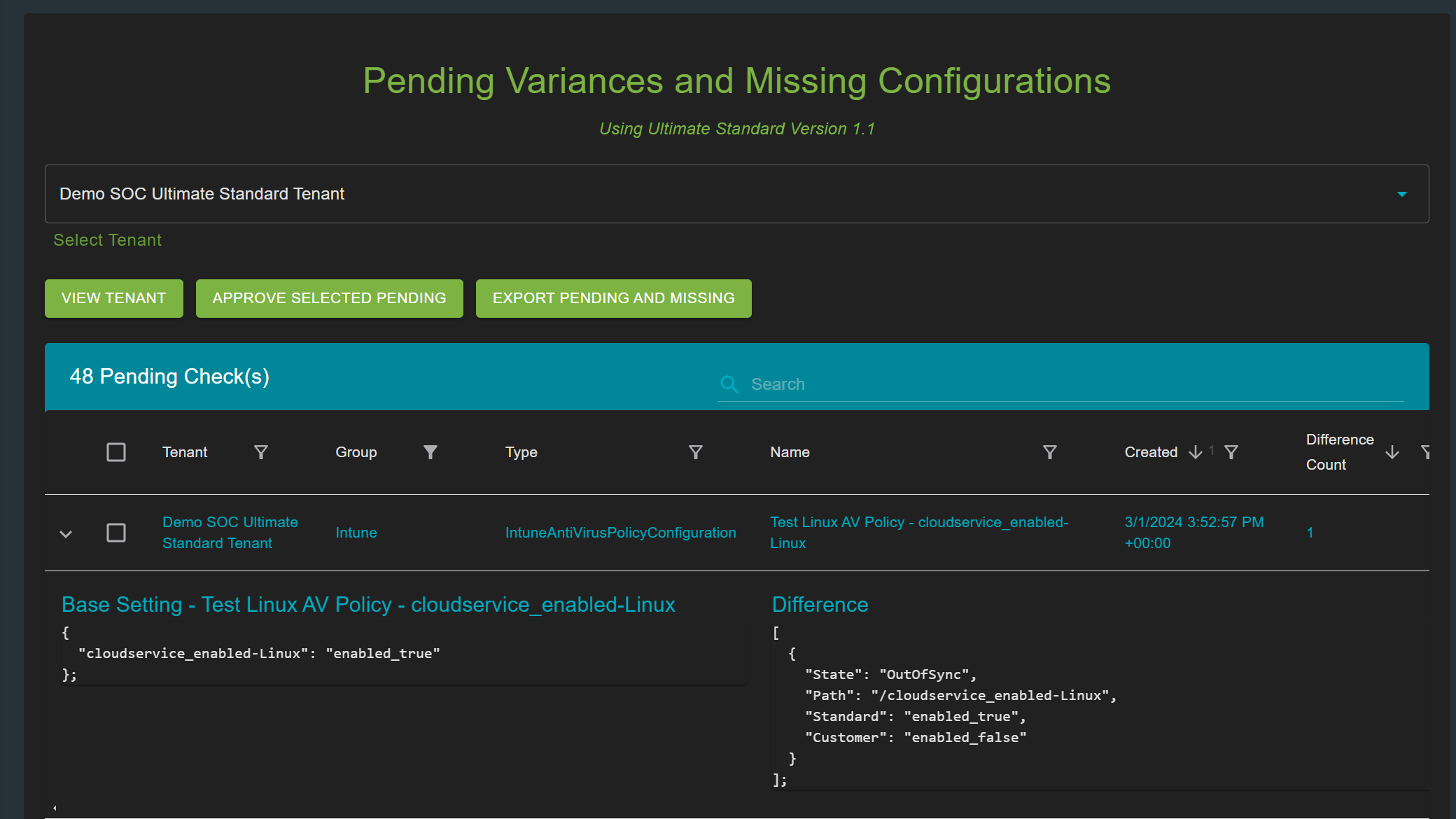
Bulletproof's flagship service, Bulletproof 365 Enterprise, brings MXDR security to organizations with 24/7 investigation and response to help them confidently navigate an evolving security landscape. Already, the new partnership has further revolutionized this service with a new feature, Drift Detector. "Drifts" due to technology updates can leave a gap and cause security risks. The Drift Detector solution, available to Bulletproof 365 Enterprise (B365E) customers, strengthens the security configuration of a customer by automatically reporting setting deviations to the Security Operations Center (SOC) team at Bulletproof.
In today's rapidly evolving landscape, managing the vast array of security infrastructure and information is a daunting task, with thousands of items requiring attention each day this can become an impossible feat without the support of a reliable partner like CWSI.
CWSI has a team of robust Microsoft Security experts, making collaboration with them highly rewarding and together, we engage in productive interactions of ideas, aiming to elevate the level of security automation delivered to CWSI's customers.
Thanks to the synergy of analytics & automation tools from Senserva and the exceptional suite of Microsoft Security Products, we ensure our customers are well-equipped to navigate and protect against the complexities of the modern security landscape.
CWSI is Senserva Partner for Ireland, the UK, Belgium and the Netherlands
Brave North Technology specializes in providing high quality, budget sensible professional technology services and support for small to mid-size businesses and nonprofits. Whether you need help designing and setting up the best IT system, diagnosing and fixing problems as they arise, protecting against security threats, or optimizing your systems to work more efficiently, Brave North Technology can help with it all.
Brave North Technology works with Senserva and its solutions to automate customer security and keep clients informed regarding technology security protocols.
















 Mark's Nomination Blog
Mark's Nomination Blog